Birth of Nmap: The Brainchild of Fyodor

In 1997, Gordon Lyon, commonly known by his pseudonym Fyodor, embarked on a mission to create a tool that could provide comprehensive insights into the security posture of networks, hence, this was the birth of the best internal network pentest tool. Fyodor, a computer science student at the time, envisioned a versatile and powerful utility that could go beyond traditional port scanning, offering security professionals a holistic view of their network environments.
Be sure to read my post on using NMAP with python and GO – here, and for a list of what I think are some of the best internal network pentest tools.
Version 1.00: The Inception
The first official release of Nmap, version 1.00, emerged in September 1997. It laid the foundation for what would later become the go-to tool for network exploration and security auditing. Even in its initial iteration, Nmap showcased Fyodor’s commitment to flexibility and functionality, setting the stage for its evolution into the best internal network pentest tool.
Early Features and Capabilities

Nmap’s early versions focused primarily on fundamental network reconnaissance techniques. It introduced essential port scanning methods, such as TCP connect scanning and SYN stealth scanning, providing users with a means to identify open ports and services running on target machines.
The Nmap Scripting Engine (NSE) Emerges
One of the pivotal moments in Nmap’s evolution occurred with the introduction of the Nmap Scripting Engine (NSE). This scripting language, introduced in 2008 with Nmap version 4.76, marked a significant leap forward. NSE empowered users to extend Nmap’s capabilities through automation and customization, elevating it to the status of the best internal network pentest tool.
The NSE allowed security professionals to craft scripts for a myriad of tasks, including vulnerability scanning, service enumeration, and even specialized activities like brute-force attacks. This newfound flexibility made Nmap not just a scanner but a dynamic and adaptable tool for various penetration testing scenarios.
The best internal network pentest tool has a lot of scripts :
| NSE Script | Description | Command Example |
|---|---|---|
| vuln | Detects vulnerabilities on a target by running various scripts. | nmap --script vuln <target> |
| default | Provides a default set of scripts, including service version detection and host discovery. | nmap --script default <target> |
| version | Focuses on service version detection, providing detailed information about the services running on open ports. | nmap --script version <target> |
| brute | Performs brute-force attacks to test the robustness of credentials on the target system. | nmap --script brute --script-args userdb=<user_file>,passdb=<pass_file> <target> |
| dns-zone-transfer | Attempts to perform a DNS zone transfer, revealing information about domain names and their associated DNS records. | nmap --script dns-zone-transfer <target> |
| http-enum | Enumerates information from HTTP services, extracting details like web server banners, directories, and server technologies. | nmap --script http-enum <target> |
| ftp-anon | Checks if an FTP server allows anonymous access, revealing potential security risks. | nmap --script ftp-anon <target> |
| ssl-enum-ciphers | Enumerates supported SSL/TLS ciphers on a target’s services, aiding in SSL/TLS security assessments. | nmap --script ssl-enum-ciphers <target> |
| smtp-enum-users | Enumerates valid email addresses through SMTP, assisting in identifying potential targets for social engineering attacks. | nmap --script smtp-enum-users <target> |
| snmp-enum | Enumerates information from SNMP services, providing details about network devices and their configurations. | nmap --script snmp-enum <target> |
These scripts showcase the breadth of Nmap’s capabilities and how the NSE can be leveraged for targeted and specialized penetration testing tasks. Feel free to explore the documentation linked in the table for more in-depth information on each script.
Open Source Spirit
Integral to Nmap’s success is its open-source nature. Fyodor’s decision to release Nmap with an open-source license fostered a vibrant community of developers, security enthusiasts, and researchers. This collaborative ecosystem contributed to the tool’s continuous refinement, ensuring that it remained at the forefront of network security. Open-source helped make nmap the best internal network pentest tool.
Accolades as the best internal network pentest tool
Over the years, Nmap has received numerous accolades and acknowledgments within the cybersecurity community. Its effectiveness and reliability have been recognized through awards like “Information Security Product of the Year” by Linux Journal, Info World, and Codetalker Digest. Such accolades reflect the impact and importance of Nmap in securing networks worldwide.
The Language of Nmap: C and Lua
Nmap’s core components are predominantly written in the C programming language, known for its efficiency and performance. Fyodor’s choice of C allows Nmap to deliver robust and fast execution, crucial for tasks like port scanning and network exploration. The decision to use C reflects a commitment to creating a tool that not only provides comprehensive functionality but does so with speed and precision.
While the core functionalities are coded in C, Nmap extends its capabilities through the Lua programming language. Lua is a lightweight scripting language that is embedded within Nmap to power the Nmap Scripting Engine (NSE). This combination of C and Lua contributes to Nmap’s versatility, offering a balance between low-level control and high-level scripting flexibility.
Understanding Nmap’s Operation
Nmap operates based on a set of well-defined and sophisticated techniques, all aimed at gathering comprehensive information about a target network. Here’s a breakdown of how Nmap works:
In the ever-evolving landscape of cybersecurity, having a versatile and powerful internal network penetration testing tool is not just an advantage—it’s a necessity. Amidst numerous options, one tool stands out as the undisputed champion: Nmap. Renowned for its unmatched efficacy and adaptability, Nmap has rightfully earned the title of the best internal network pentest tool, proving indispensable for security professionals globally.
Navigating Nmap’s Versatility
At the core of Nmap’s supremacy lies its ability to conduct comprehensive network reconnaissance. Armed with an array of techniques, Nmap unveils intricate details about a target network, empowering security professionals to pinpoint vulnerabilities and potential entry points. The cornerstone of Nmap’s functionality lies in its port scanning capabilities – a meticulous process that probes a target’s ports to unveil whether they are open, closed, or filtered.
Diverse scanning techniques, including TCP connect scanning, SYN stealth scanning, and UDP scanning, make up Nmap’s arsenal. These techniques provide security professionals with a comprehensive overview of a network’s security posture. Identifying open ports becomes a linchpin in security assessments, as these ports often serve as potential gateways for malicious actors. Going beyond mere port scanning, Nmap delves into service version detection, shedding light on the specific applications and services running on open ports.
The Nmap Scripting Engine (NSE):
To solidify its status as best internal network pentest tool, Nmap introduces the Nmap Scripting Engine (NSE), a powerful scripting language that propels its capabilities to unparalleled heights. NSE empowers security professionals to automate and customize tasks, rendering it an invaluable asset during penetration testing endeavors.
The NSE boasts an extensive script database, encompassing a diverse range of scripts designed for various purposes. Whether it’s vulnerability detection, credential brute-forcing, or host discovery, NSE scripts offer a flexible and efficient means of tailoring Nmap’s functionality to meet specific testing requirements.
Commanding NSE: Unleashing Advanced Commands
1. Vulnerability Scanning
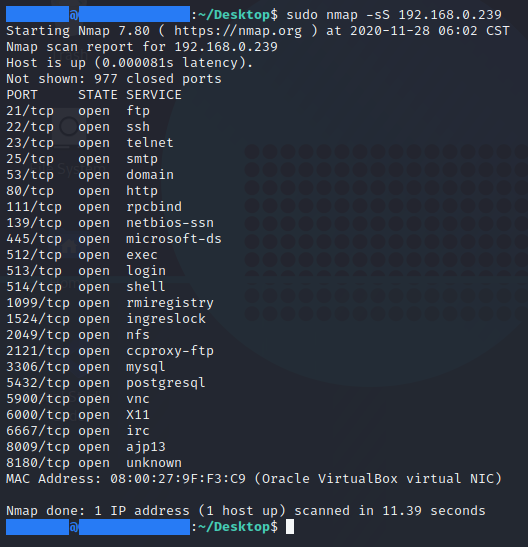
Identifying vulnerabilities forms the bedrock of effective penetration testing. Nmap’s NSE can be harnessed for this purpose using scripts dedicated to vulnerability scanning. The following command exemplifies how Nmap can be configured to unveil potential vulnerabilities:
nmap -p 1-65535 --script vuln <target>This command orchestrates a comprehensive scan across all ports, executing scripts categorized under “vuln.” The result is a detailed report exposing potential weaknesses within the target system.
Alternatively, if you’d like to see an output of what an NSE scan looks in a GUI format, like on Zenmap, then take a look below. I’d recommend Zenmap if you are just starting out as a pentester or infosec analyst, and are not yet familiar with nmap scripting. Here’s an example output :
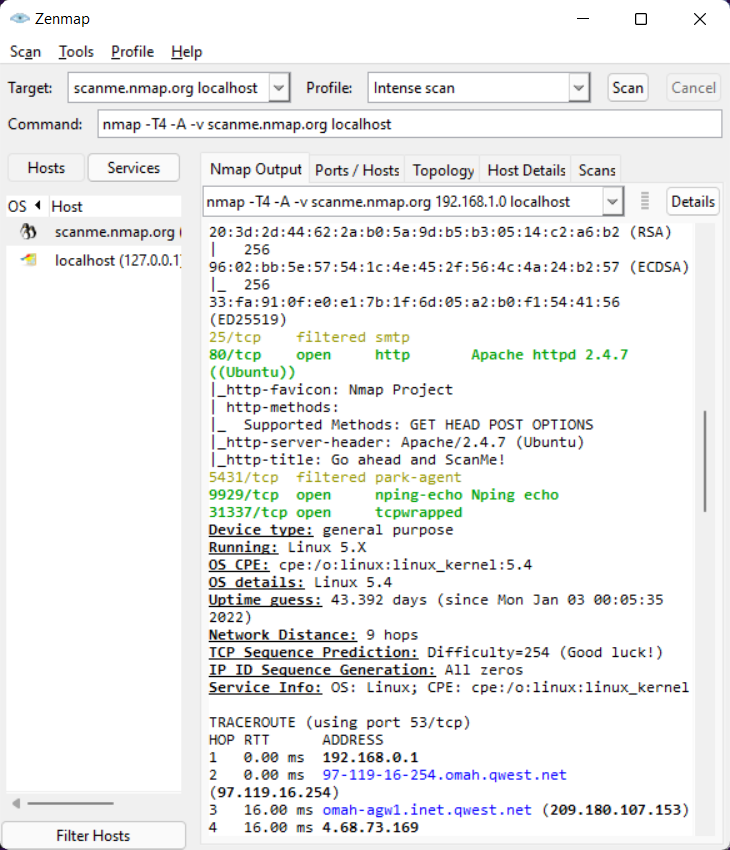
2. Service Enumeration w/ best internal network pentest tool
For a holistic internal network penetration test, understanding the services running on open ports is crucial. Nmap’s NSE facilitates service enumeration with the following command:
nmap -p 1-65535 --script default,version <target>This command merges default scripts with version detection, offering detailed insights into the services operational on open ports. This intelligence proves invaluable for security professionals seeking to discern the specific attack vectors available to potential adversaries.
3. Brute-Force Attacks w/ the best internal network pentest tool
Testing the resilience of passwords through brute-force attacks is a fundamental aspect of penetration testing. Nmap’s NSE provides scripts tailored for this purpose, as demonstrated by the following command:
nmap --script brute --script-args userdb=<user_file>,passdb=<pass_file> <target>This command leverages NSE scripts to execute brute-force attacks, systematically testing the robustness of credentials on the target system. Such tests are essential for organizations aiming to fortify their defenses against unauthorized access.
Unveiling the Multifaceted Nmap Advantage
Nmap’s excellence extends beyond its role as a penetration testing tool, encompassing a multitude of facets that contribute to its unrivaled position in the cybersecurity realm.
1. Flexibility and Power: The Backbone of Nmap
Nmap’s flexibility is a testament to its support for dozens of advanced techniques, including mapping out networks with IP filters, firewalls, routers, and other obstacles. This encompasses a spectrum of port scanning mechanisms (both TCP & UDP), OS detection, version detection, ping sweeps, and more. The documentation page serves as a comprehensive resource for exploring the extensive capabilities Nmap offers.
# Example of TCP connect scanning
nmap -sT <target>
# Example of SYN stealth scanning
nmap -sS <target>
# Example of UDP scanning
nmap -sU <target>The tool’s power is exemplified by its capability to scan colossal networks comprising hundreds of thousands of machines. This scalability positions it as a top choice for security professionals grappling with large and complex network infrastructures.
2. Portability and User-Friendliness: A Seamless Experience
Nmap’s portability is another distinctive advantage. It supports a plethora of operating systems, including Linux, Microsoft Windows, FreeBSD, OpenBSD,
Solaris, IRIX, Mac OS X, HP-UX, NetBSD, Sun OS, Amiga, and more. The ease of use is evident in both its traditional command line and graphical (GUI) versions, providing options to suit user preferences.
# Example of basic command line usage
nmap -v -A <target>
# Example of GUI version usage
nmap -v -A -oN output.txt <target>3. Free and Well-Documented: Empowering the Community as the best internal network pentest tool
In alignment with its commitment to internet security, the Nmap Project offers the tool for free download, accompanied by full source code that users can modify and redistribute under the terms of the license. The project’s primary goals include making the internet more secure and providing advanced tools for network exploration. The docs on NMAP are vastless, also another reason it’s best internal network pentest tool.
Nmap’s extensive documentation further enhances its user-friendly nature. Comprehensive and up-to-date man pages, whitepapers, tutorials, and even a dedicated book contribute to a wealth of knowledge available to users in multiple languages.
# Example of accessing Nmap man page
man nmap4. Community Support and Acclaim: A Testimony to Reliability
While Nmap comes with no warranty, its robust community support is a testament to its reliability. Developers and users actively engage on Nmap mailing lists, contributing to the tool’s ongoing refinement. Various accolades, including “Information Security Product of the Year” by Linux Journal, Info World, and Codetalker Digest, highlight Nmap’s acclaim in the cybersecurity realm. The tool is widely known in the community and has taken many updates from open source community members, making it the best internal network pentest tool!
# Example of engaging with the Nmap community
# Join the Nmap mailing list for discussions and support5. Popularity as the best internal network pentest tool
Nmap’s popularity transcends the cybersecurity community, finding its way into magazine articles, motion pictures, books, and even a comic book series. Its widespread recognition underscores its significance and impact in the field.
The Journey Ahead: Nmap’s Ongoing Evolution
As the cybersecurity landscape continues its dynamic evolution, Nmap remains at the forefront, adapting and expanding its capabilities to meet emerging challenges. Its open-source nature ensures a collaborative and vibrant community, contributing to its ongoing refinement.
Nmap’s status as the best internal network pentest tool is not just a label; it’s a testament to its continuous evolution and adaptability. Its robust port scanning capabilities, coupled with the flexibility and power of the NSE, make it an indispensable asset for security professionals. In an era where cybersecurity is non-negotiable, Nmap stands tall as a stalwart guardian of network integrity, empowering defenders to stay one step ahead of potential threats. Nmap doesn’t just lead the pack; it defines the very essence of what the best internal network pentest tool should be.
Leave a Reply